
An In-Depth Analysis of Conti Ransomware
A detailed exploration of Conti ransomware’s TTPs based on leaked internal documentation
Imagine you’re a successful business owner, and it’s midnight when your phone vibrates with an urgent alert. Your entire organization has gone dark. Emails, databases, and nothing works. Only a ransom note appears, demanding millions. It’s not just one ransomware group, it’s a coordinated attack by LockBit, Akira, and Clop, names that can be every business nightmare.
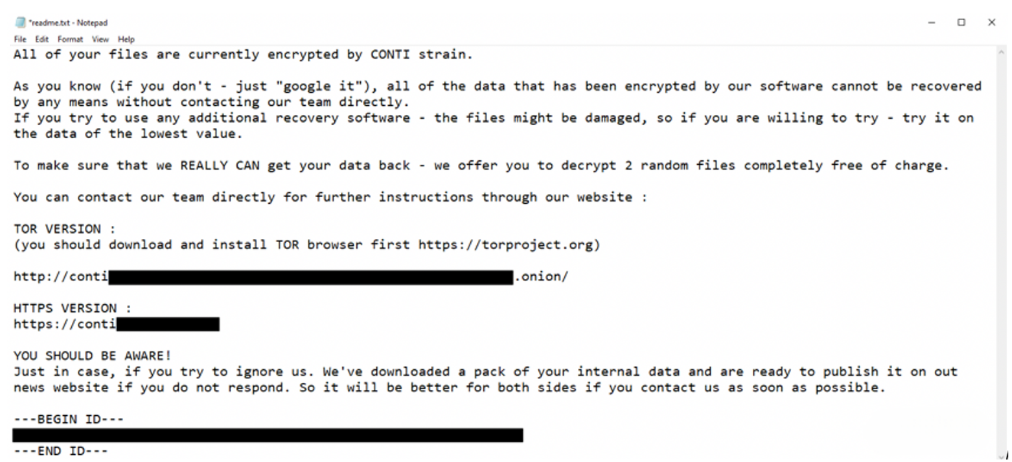
Ransomware attacks have evolved from opportunistic schemes to highly sophisticated operations, often orchestrated by well-funded and organized cybercrime syndicates. Among these, the Conti ransomware group stands out as one of the most notorious and successful. With estimated revenues exceeding $200 million, Conti has inflicted substantial damage on businesses worldwide.
In this article, we delve into the inner workings of Conti, exploring their tactics, techniques, and procedures (TTPs), as well as the tools they employ to execute their attacks. Our analysis is based on leaked internal documentation, offering a rare glimpse into the operations of a modern ransomware group.
The Rise of Conti Ransomware
Conti emerged on the cybercrime scene in 2020, quickly establishing itself as a formidable threat. The group is believed to be managed by Wizard Spider, a Russia-based cybercrime organization also linked to the Ryuk ransomware. Operating under a ransomware-as-a-service (RaaS) model, Conti recruits affiliates to distribute the ransomware in exchange for a share of the profits. This decentralized approach has enabled rapid scaling, with affiliates targeting organizations across various industries.
Ransomware-as-a-Service: The Business of Conti
Conti’s operations resemble those of a legitimate business, complete with hierarchical structures, specialized roles, and even a “CEO” overseeing activities. New affiliates undergo an onboarding process where they receive detailed manuals and training on the group’s methodologies. These documents outline everything from network infiltration techniques to evasion strategies and maximizing ransom payouts.
Conti’s Tactics, Techniques, and Procedures (TTPs)
The leaked Conti documentation reveals a list of TTPs employed throughout their attack lifecycle. Understanding these tactics can help organizations improve their defenses and respond more effectively to ransomware incidents.
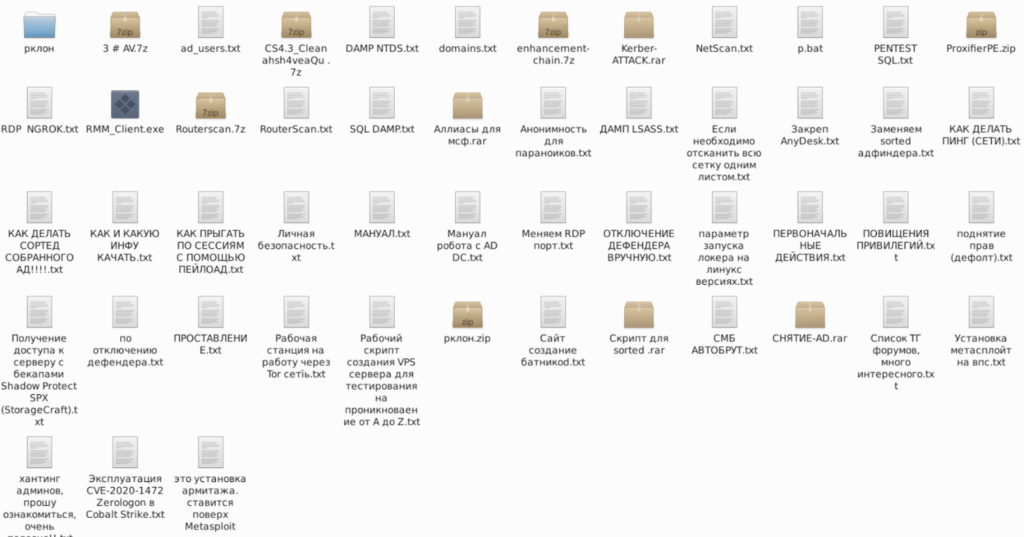
Initial Access and Lateral Movement
Conti’s primary objective is to gain a foothold within the target network and escalate privileges until they control the domain controller (DC). They exploit weak credentials, unpatched vulnerabilities, and social engineering tactics. Key vulnerabilities exploited include:
- PrintNightmare (CVE-2021-1675/CVE-2021-34527) – A Windows Print Spooler vulnerability allowing remote code execution.
- ZeroLogon (CVE-2020-1472) – A flaw in the Netlogon protocol enabling attackers to gain administrative control.
- EternalBlue (MS17-010) – An SMB protocol exploit used for remote code execution and lateral movement.
Once inside, Conti operators steal credentials and expand access, aiming to gain domain administrator privileges. They exfiltrate sensitive data such as login logs, DNS records, and password hashes.
Post-Exploitation Activities
After establishing control, Conti operators maintain persistence using privilege escalation exploits, including:
- CVE-2018-8120 – A Windows privilege escalation vulnerability.
- CVE-2019-0841 – A flaw allowing unauthorized privilege elevation.
- CVE-2021-1675 – Another component of the PrintNightmare exploit.
Tools and Command-Line Utilities
Conti’s toolkit blends well-known offensive security tools, legitimate software, and custom scripts. Key tools include:
- Cobalt Strike Beacon – A post-exploitation framework for command-and-control (C2).
- ATERA Agent – A remote management tool repurposed for persistence.
- Ngrok – A tunneling tool used for stealthy data exfiltration.
- RClone – An open-source tool for transferring stolen data to cloud storage.
- Mimikatz – A credential theft tool extracting plaintext passwords and Kerberos tickets.
- PowerShell – Used for automation, disabling security features, and executing payloads.
- Kerberoasting – A technique for extracting and cracking service account credentials from Active Directory.
Evading Detection
One particularly effective technique I see often involves using AnyDesk, a legitimate remote access tool repurposed by attackers to maintain persistent access and evade detection silently.
The attackers leveraged a PowerShell script to download AnyDesk to the C:\ProgramData\ directory, where it was silently installed with commands that ensured it launched with Windows and operated without user prompts.
A predefined password was set via the command line, and the attackers created a hidden administrator account by modifying the registry (SpecialAccounts\UserList) and adding the account to the local Administrators group, keeping it hidden from the login screen.
Lastly, they retrieved the system’s AnyDesk ID using the —get-id parameter, enabling stealthy, persistent remote control of the infected host without raising immediate red flags in standard monitoring tools.
Conclusion
The Conti ransomware group displays modern cybercrime as organized, professional, and highly effective. Organizations can better prepare to defend against such threats by understanding their tactics and tools. While ransomware remains a persistent challenge, staying informed and proactive is key to minimizing risk.
Our experts can help assess vulnerabilities, implement robust security measures, and respond effectively to incidents. Professional assistance is essential for organizations overwhelmed by the complexity of ransomware defense.
Don’t wait until it’s too late - take action now to protect your business from the growing ransomware threat.
References:
https://en.wikipedia.org/wiki/PrintNightmare
https://www.thehacker.recipes/ad/movement/print-spooler-service/printnightmare
https://en.wikipedia.org/wiki/Conti_(ransomware)
https://www.cisa.gov/news-events/alerts/2021/09/22/conti-ransomware
More Articles
Continue reading about cybersecurity

