
Hacking for the Right Reasons
The Myth of Security in Open Source Software and 11 CVEs Uncovered in Masa CMS
Hello Everyone,
Today, I’m sharing a research project I worked on back in 2023 that nearly went unnoticed but definitely deserves attention.
Security research isn’t always glamorous. Most of the time, it’s quiet work, hours spent reading code someone else wrote, testing inputs, reading docs, and thinking like an attacker and how to abuse functions so the bad guys won’t exploit that.
At Zero-Defense Labs, this is what we do. We identify vulnerabilities before they become real-world threats. No noise. Just impact.
Sometime in 2023, during one of the busiest periods of the year, I started poking around Masa CMS, an open-source content management system.
Just curiosity and that familiar instinct when a system “smells” like it might have something interesting under the hood.
What started as a curiosity-led dive quickly escalated.
CVEs List
In that single hacking session, 11 vulnerabilities were discovered.
I might share more soon, so stay tuned.
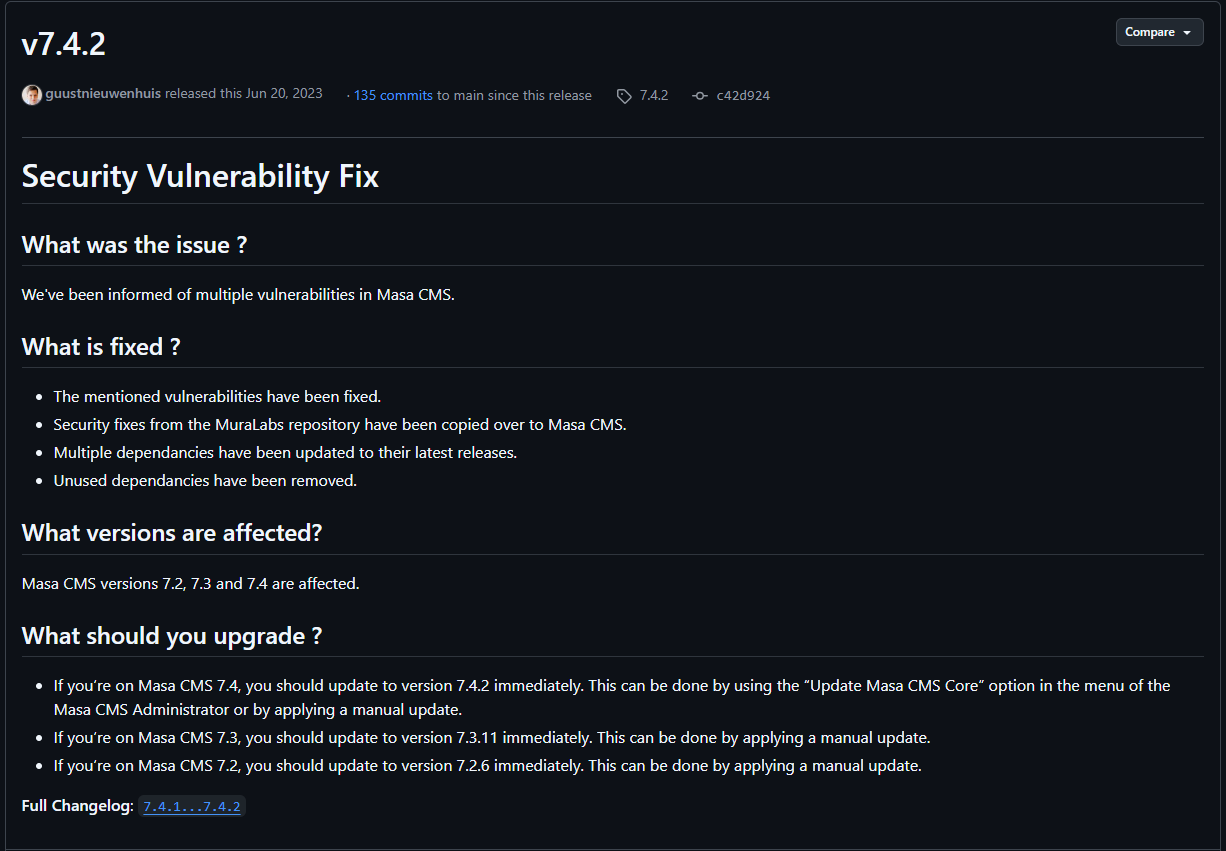
Security fixes are available in versions 7.4.2, 7.3.11, and 7.2.6.
CVE-2023-29682: Open Redirect Vulnerability.
CVE-2023-29683: Authenticated Stored XSS Vulnerability.
CVE-2023-29684: Authenticated DOM-based XSS Vulnerability.
CVE-2023-29685: Stored XSS in the Collections Component.
CVE-2023-29686: XML External Entity (XXE) Vulnerability in Upload and Install Plugins.
CVE-2023-31832: Open Redirect Vulnerability in URL Parsing.
CVE-2023-31833: Authenticated Stored XSS via Title Injection.
CVE-2023-31834: No Session Termination when Logging Out Vulnerability.
CVE-2023-31835: User Enumeration Vulnerability.
CVE-2023-31836: Cross-Site Request Forgery (CSRF) in Email Settings could lead to ATO.
CVE-2023-31837: ZIP Slip Vulnerability in Upload and Install Plugins allows you writing as root.
Open Source ≠ Security
Open-source software is often praised for its transparency and collaborative development, but transparency doesn’t guarantee security. Just because the code is publicly available doesn’t mean it’s been thoroughly reviewed or is free from vulnerabilities.
In fact, open-source projects are just as susceptible, if not more so, to critical flaws, especially when security isn’t a core priority.
I won’t delve into each individual vulnerability I discovered in Masa CMS, which would take far too long, so in this post, I will highlight two particularly critical ones to illustrate the risks involved.
What is Mura Software?
Mura Software is the company behind Mura CMS, an open-source, enterprise-grade content management system.
What is Masa CMS?
Masa CMS is an open-source enterprise content management platform built on the final freely available version of Mura CMS.
When Installing Plugins Become Dangerous
While exploring Masa CMS, I discovered something worth reviewing. The CMS included a feature to upload custom plugins. A functionality that, from an attacker’s perspective, presented a potential entry point. I focused on this attack vector and quickly developed a malicious plugin, which I successfully uploaded to the system.
I leveraged their Google Site Maps plugin.
https://github.com/MasaCMS/MasaGoogleSitemaps
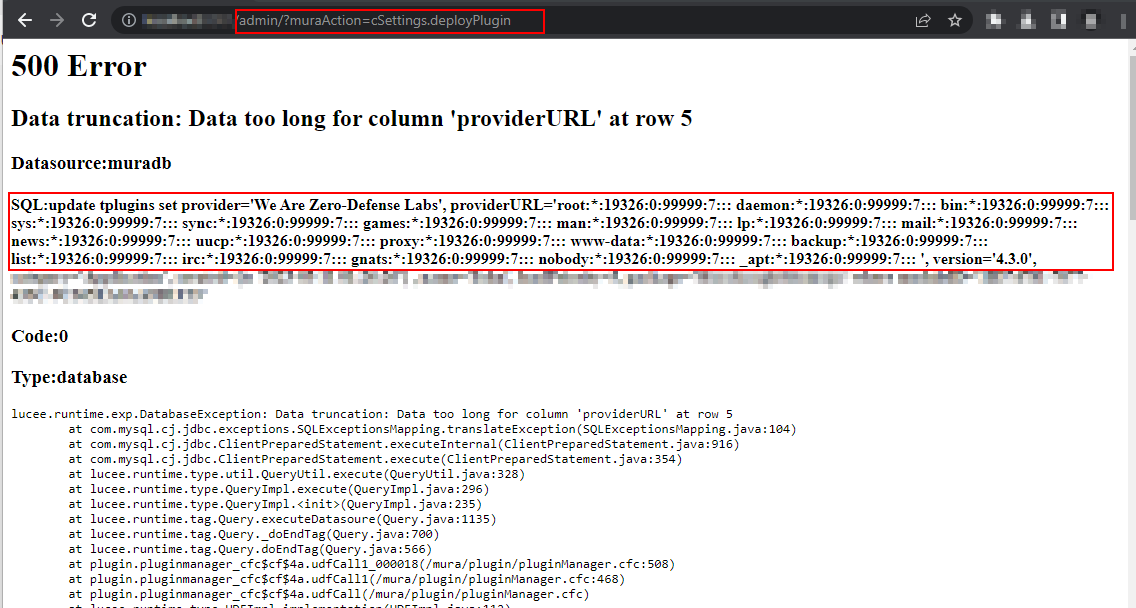
First, the plugin allowed an XXE (XML External Entity) injection, which meant I could read arbitrary files on the server, anything from configuration files to sensitive credentials.
But I didn’t stop there.
Digging deeper, I found the CMS vulnerable to a ZIP Slip attack. I could write files outside the intended directory by carefully crafting a ZIP file, even overwriting system files. This could let an attacker write files as root, which is a dangerous privilege escalation.
Chaining a few of these vulnerabilities can lead to an account takeover and even a reverse shell, ultimately granting complete control over the CMS server. I’ve chosen not to disclose more from the technical details to prevent potential abuse.
What is XXE?
XXE (XML External Entity Injection) is a security vulnerability when an application processes XML input insecurely. It allows attackers to read local files, perform internal port scanning, or execute remote code by injecting malicious XML.
Proof Of Concept - XXE
Deploying the Malicious Plugin with an XXE Payload
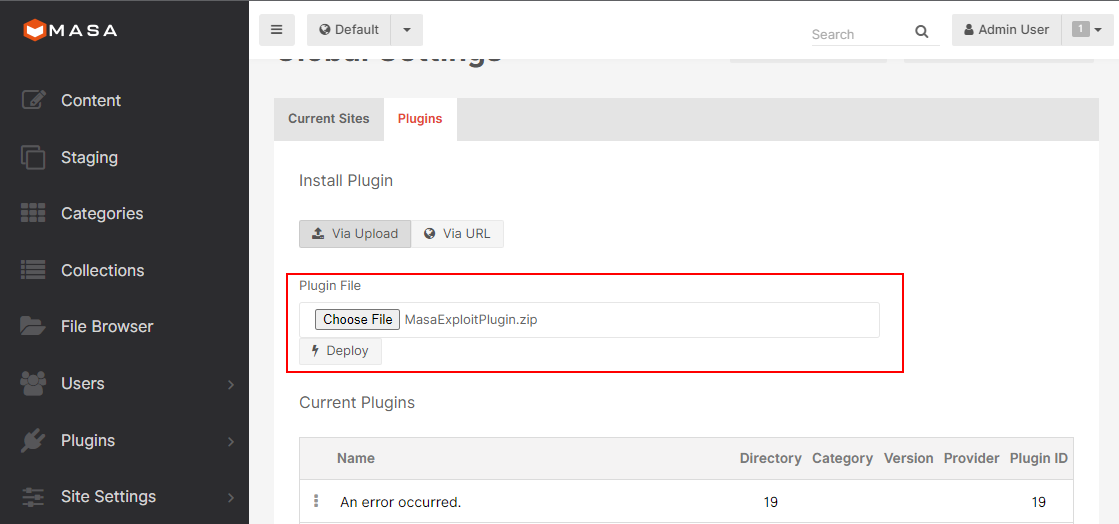
The error message reveals the contents of /etc/passwd, confirming successful exploitation.
What is a Zip Slip?
Zip Slip is a path traversal vulnerability when extracting archive files without properly validating file paths. An attacker can craft a zip file with file names designed to overwrite system files or place malicious files outside the intended directory.
Proof of Concept - Zip Slip
The Malicious Plugin Containing a the payload
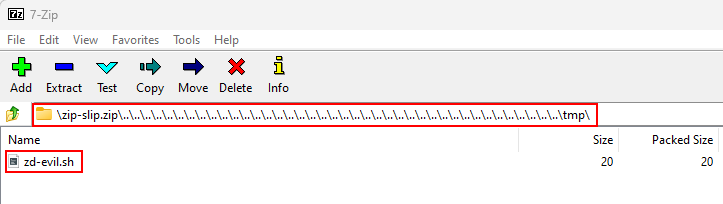
Upload a ZIP file that includes the payload.
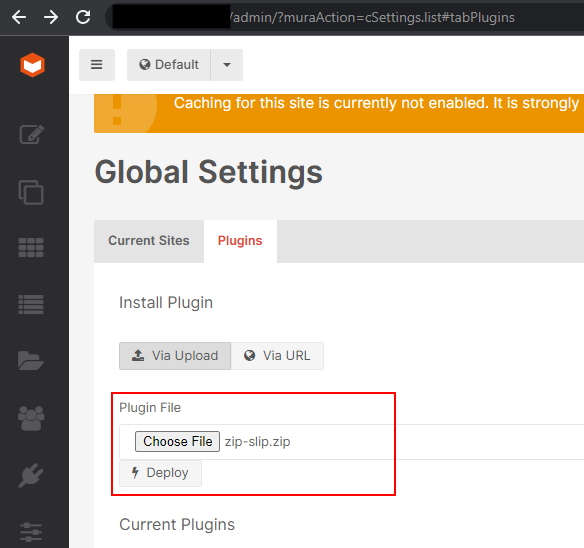
Note: A 500 Server Error might give the impression that the exploit failed.
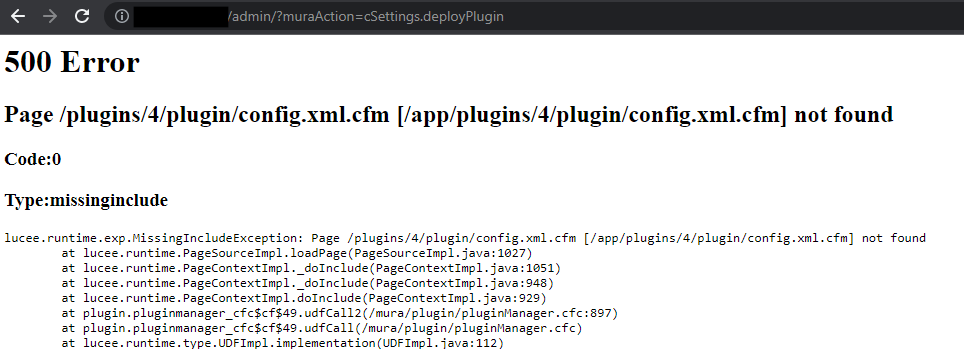
In reality, the exploit executes as intended despite the error response.
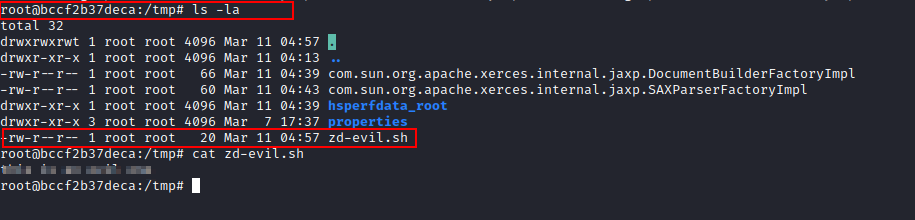
If you want to review the vulnearble code you can view the commit: https://github.com/MasaCMS/MasaCMS/commit/2c282aaf023f4cdf26996766c23e5396d959e4c2
Responsible Disclosure
I responsibly reported the vulnerabilities by submitting detailed documentation, proof-of-concept (PoC) code, and a comprehensive report.
The team acknowledged the findings.
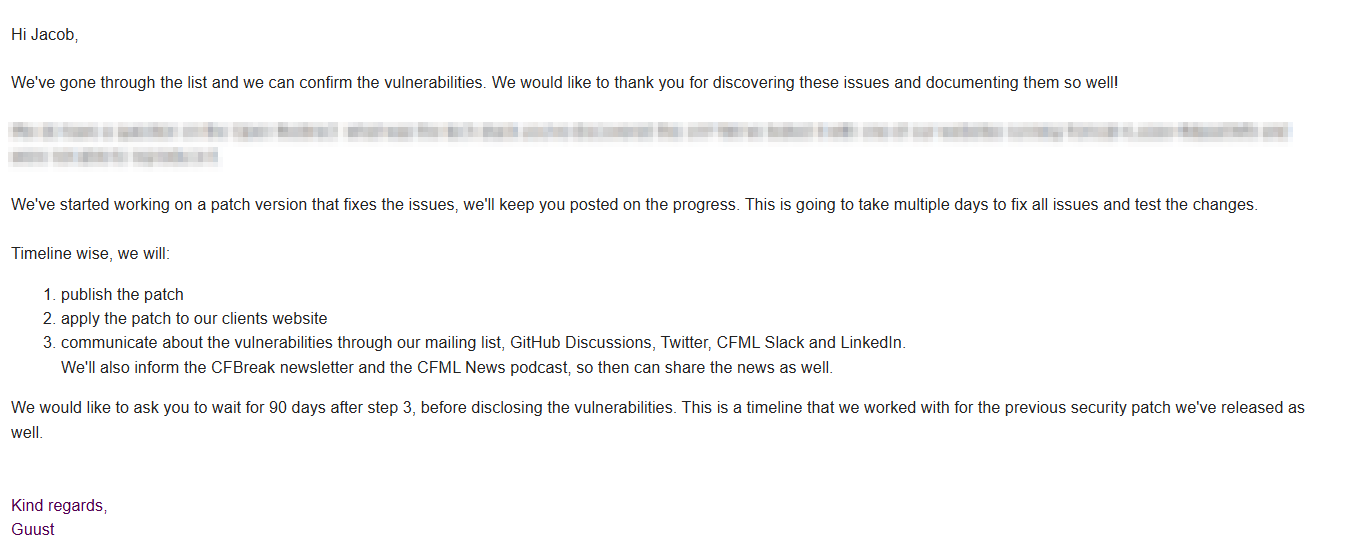
During further discussions, it was discovered that the vulnerabilities also affected older versions of the software and another related platform, Mura CMS, which may result in a separate CVE being issued.
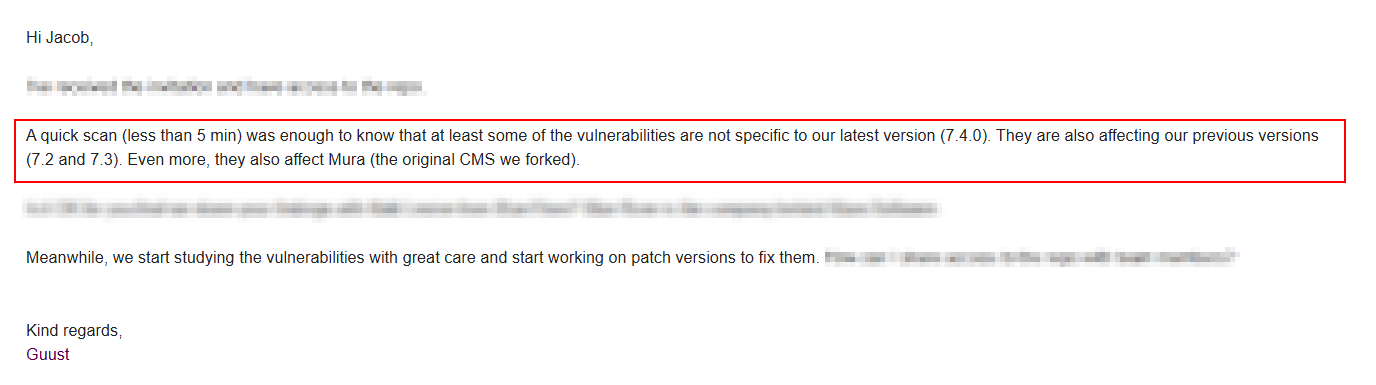
And while I did report everything responsibly, and the issues were eventually fixed, no formal credit was given either.
Conclusion
This experience is a reminder that even widely used software can hold critical vulnerabilities, sometimes for years, without being detected. It highlights why regular security assessments and penetration testing are critical, not just optional.
Relying solely on developers, no matter how skilled, is not enough. Security must be a dedicated focus, with independent reviews and continuous attention.
Organizations must never install plugins without verifying their source and reviewing their code.
A single unchecked plugin can compromise an entire system.
To those in the community, keep looking, testing, and reporting. Every vulnerability you find and disclose responsibly strengthens the entire ecosystem. Security is a shared responsibility, and your efforts truly make a difference.
References
https://github.com/MasaCMS/MasaCMS
https://github.com/MasaCMS/MasaCMS/discussions/202
https://github.com/MasaCMS/MasaCMS/releases/tag/7.4.2
https://github.com/MasaCMS/MasaCMS/compare/7.4.1…7.4.2
More Articles
Continue reading about cybersecurity

